Listen up, folks. If you're diving into the world of remote server management, securing remote SSH access should be at the top of your priority list. Imagine this: your server is like a fortress, and SSH (Secure Shell) is the gatekeeper. But if that gatekeeper isn’t properly fortified, it’s like leaving the front door wide open for digital intruders. In this guide, we’ll walk you through everything you need to know to lock down your SSH connections and keep your data safe. So buckle up, because we’re about to deep-dive into the nitty-gritty details.
SSH might sound like a fancy tech term, but it’s actually pretty straightforward. It’s a protocol that allows you to securely access and manage remote servers. Think of it as a secure tunnel between your computer and the server. But here’s the catch: if not properly configured, this tunnel can become a highway for hackers. That’s why securing remote SSH access is crucial, especially in today’s digital landscape where cyber threats are lurking around every corner.
Before we dive deeper, let’s get one thing straight: this isn’t just about tech jargon. This is about protecting your business, your data, and your peace of mind. Whether you’re a seasoned IT pro or a newbie just starting out, this guide will arm you with the knowledge and tools to make your SSH connections rock-solid. Let’s get started, shall we?
Read also:Aagmaalgives The Ultimate Guide To Unlocking Generosity And Making A Difference
Table of Contents
- Understanding SSH and Its Importance
- Common SSH Attacks and How to Avoid Them
- Configuring SSH for Maximum Security
- Using SSH Keys Instead of Passwords
- Limiting SSH Access to Authorized Users
- Securing Your SSH Connections with Firewalls
- Monitoring SSH Activity for Suspicious Behavior
- Best Practices for Securing Remote SSH Access
- Troubleshooting Common SSH Security Issues
- Conclusion: Take Action and Stay Secure
Understanding SSH and Its Importance
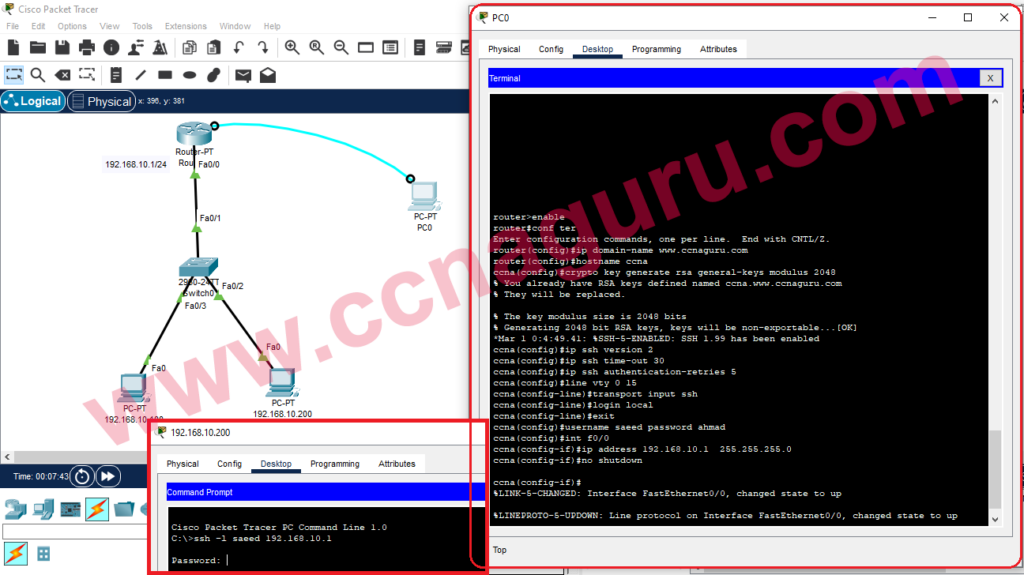
Let’s break it down. SSH stands for Secure Shell, and it’s basically a network protocol that lets you connect to remote servers securely. Picture this: you’re sitting in your cozy home office, sipping on a cup of coffee, while your server is humming away in some data center miles away. SSH is what allows you to communicate with that server as if you were physically there, but with an added layer of security.
But why is SSH so important? Well, without it, your data would be floating around the internet like a fish out of water—vulnerable and exposed. SSH encrypts all the data that flows between your computer and the server, making it much harder for hackers to intercept and misuse your information. And in a world where data breaches are becoming more common than rain in Seattle, securing remote SSH access is no longer optional—it’s a necessity.
So, how does SSH work exactly? When you initiate an SSH connection, it creates a secure tunnel between your computer and the server. This tunnel encrypts all the data that passes through it, ensuring that even if someone manages to intercept the data, they won’t be able to make sense of it without the decryption key. Pretty cool, right?
Why Securing SSH Access Matters
Here’s the deal: SSH is powerful, but it’s also a double-edged sword. If not properly secured, it can become a gateway for malicious actors to infiltrate your system. Think about it: if someone gains unauthorized access to your SSH connection, they could potentially access sensitive data, install malware, or even take control of your entire server. And nobody wants that, right?
By securing your SSH access, you’re not just protecting your data—you’re also protecting your reputation. Imagine if your customers’ information got compromised because you didn’t take the necessary precautions. That kind of breach could do serious damage to your business, both financially and reputation-wise. So yeah, securing remote SSH access isn’t just about tech—it’s about trust.
Read also:Kdarchitects Landscape Ideas By Morph Redefining Outdoor Spaces
Common SSH Attacks and How to Avoid Them
Alright, let’s talk about the bad guys. Hackers are always on the lookout for vulnerabilities, and SSH is a prime target. Here are some of the most common SSH attacks and how you can avoid falling victim to them:
Brute-Force Attacks
A brute-force attack is when a hacker tries to guess your password by systematically trying every possible combination. It’s like trying every key on your keyring until one finally fits. To avoid this, you can:
- Use strong, complex passwords that include a mix of letters, numbers, and symbols.
- Implement rate limiting to restrict the number of login attempts within a certain time frame.
- Switch to SSH keys instead of passwords (we’ll cover this in more detail later).
Man-in-the-Middle Attacks
In a man-in-the-middle attack, a hacker intercepts your SSH connection and tries to eavesdrop on your communication. To prevent this, you should:
- Always verify the server’s fingerprint before establishing a connection.
- Use SSH certificates to authenticate both the client and the server.
Port Scanning
Port scanning is when a hacker tries to identify open ports on your server to find potential vulnerabilities. To protect yourself, you can:
- Change the default SSH port (usually 22) to something less obvious.
- Use a firewall to restrict access to the SSH port.
Configuring SSH for Maximum Security
Now that we’ve covered the basics, let’s talk about how to configure SSH for maximum security. The SSH configuration file, usually located at /etc/ssh/sshd_config, is where all the magic happens. Here are some key settings you should consider:
Disable Root Login
By default, SSH allows root login, which is a big no-no from a security standpoint. To disable it, simply edit the sshd_config file and set:
PermitRootLogin no
Change the Default Port
As we mentioned earlier, changing the default SSH port can help deter automated attacks. To do this, simply edit the sshd_config file and set:
Port [your chosen port number]
Enable Two-Factor Authentication
Two-factor authentication adds an extra layer of security by requiring users to provide two forms of identification before gaining access. To enable it, you’ll need to install and configure a tool like Google Authenticator.
Using SSH Keys Instead of Passwords
One of the best ways to secure your SSH connections is by using SSH keys instead of passwords. SSH keys are like digital keys that provide a more secure and convenient way to authenticate users. Here’s how you can set them up:
Generate SSH Keys
First, you’ll need to generate a pair of SSH keys—a private key and a public key. You can do this by running the following command on your local machine:
ssh-keygen -t rsa -b 4096
Copy the Public Key to the Server
Once you’ve generated the keys, you’ll need to copy the public key to the server. You can do this by running:
ssh-copy-id user@server
Disable Password Authentication
Finally, to ensure that only SSH keys can be used for authentication, edit the sshd_config file and set:
PasswordAuthentication no
Limiting SSH Access to Authorized Users
Another important step in securing remote SSH access is limiting who can access your server. Here are some ways you can do this:
Use AllowUsers
The AllowUsers directive in the sshd_config file allows you to specify which users are allowed to connect via SSH. For example:
AllowUsers user1 user2
Restrict Access by IP Address
You can also restrict SSH access to specific IP addresses by using a firewall or by editing the sshd_config file. For example:
ListenAddress [your IP address]
Securing Your SSH Connections with Firewalls
Firewalls are like digital bouncers that control who gets in and who stays out. Here are some ways you can use firewalls to secure your SSH connections:
Use UFW (Uncomplicated Firewall)
UFW is a user-friendly firewall tool that makes it easy to configure firewall rules. To allow SSH traffic, simply run:
sudo ufw allow ssh
Restrict Incoming Connections
To further enhance security, you can restrict incoming SSH connections to specific IP addresses. For example:
sudo ufw allow from [your IP address] to any port 22
Monitoring SSH Activity for Suspicious Behavior
Even with all these security measures in place, it’s important to keep an eye on your SSH activity for any suspicious behavior. Here are some tools and techniques you can use:
Use Log Files
SSH logs all connection attempts in the /var/log/auth.log file. Regularly reviewing these logs can help you identify any unauthorized access attempts.
Implement Intrusion Detection Systems
Intrusion detection systems (IDS) can automatically monitor your SSH connections for suspicious activity and alert you if anything unusual is detected.
Best Practices for Securing Remote SSH Access
Here are some additional best practices to keep in mind when securing your SSH connections:
- Regularly update your SSH software to ensure you have the latest security patches.
- Use strong, unique passwords for all user accounts.
- Limit the number of SSH connections allowed at any given time.
- Regularly review and update your SSH configuration to address any new security concerns.
Troubleshooting Common SSH Security Issues
Even with the best-laid plans, things can still go wrong. Here are some common SSH security issues and how to troubleshoot them:
Connection Refused
If you’re getting a “connection refused” error, it could mean that the SSH service isn’t running or that the port is blocked by a firewall. Check the status of the SSH service and ensure that the firewall rules are correctly configured.
Permission Denied
A “permission denied” error usually indicates that there’s an issue with your authentication method. Double-check your SSH keys and ensure that password authentication is enabled if you’re using passwords.
Conclusion: Take Action and Stay Secure
And there you have it, folks. Securing remote SSH access might seem like a daunting task, but with the right tools and knowledge, it’s definitely doable. By following the steps outlined in this guide, you’ll be well on your way to fortifying your SSH connections and keeping your data safe from prying eyes.
So what are you waiting for? Take action today and make securing remote SSH access a priority. And don’t forget to share this guide with your friends and colleagues—after all, knowledge is power. Until next time, stay safe out there!