Imagine this: you're managing IoT devices scattered across the globe, but you need to access them securely from anywhere in the world. That's where RemoteIoT device SSH tutorial comes into play. SSH, or Secure Shell, is your golden ticket to remote access, and mastering it can transform how you handle your IoT infrastructure. Whether you're a seasoned IT pro or just dipping your toes into the IoT waters, this guide has got you covered.
But why SSH, you ask? Well, let me tell ya, SSH isn't just another buzzword in the tech world. It's a rock-solid protocol designed to keep your data safe while you're tinkering with devices miles away. And when it comes to IoT, security isn't optional—it's a must. In this tutorial, we're gonna break down everything you need to know about setting up SSH for your RemoteIoT devices, step by step, so even if you're new to this game, you'll feel like a pro in no time.
Now, buckle up because we're diving deep into the world of SSH and RemoteIoT devices. By the end of this tutorial, you'll have the skills to securely manage your IoT fleet, troubleshoot issues on the fly, and keep your data as safe as Fort Knox. So, let's get started, shall we?
Read also:What Is A Crown Family Exploring The Royal Dynasty And Its Legacy
Table of Contents
- Introduction to SSH
- Why SSH for RemoteIoT Devices?
- Setting Up SSH on Your RemoteIoT Device
- Securing Your SSH Connection
- Troubleshooting SSH Issues
- Advanced SSH Features for RemoteIoT
- Best Practices for SSH Management
- Automating SSH Tasks
- The Future of SSH in IoT
- Conclusion
Introduction to SSH
Alright, let's start with the basics. What exactly is SSH, and why should you care? SSH, or Secure Shell, is a network protocol that allows you to securely access a remote device over an unsecured network. Think of it like a secret tunnel that lets you communicate with your devices without anyone eavesdropping. It's been around since the '90s, and it's still one of the most reliable ways to manage remote systems.
Here's the deal: SSH encrypts all data transferred between your computer and the remote device, which means even if someone intercepts the communication, they won't be able to make sense of it. And that's huge, especially when you're dealing with sensitive IoT data. But don't worry, we'll dive deeper into how SSH works and why it's so important for RemoteIoT devices in the next sections.
How SSH Works
Now, let's talk about the nitty-gritty of how SSH actually works. When you initiate an SSH connection, your computer and the remote device exchange keys to establish a secure session. These keys are like digital passwords that ensure only authorized users can access the device. Once the connection is established, everything you do—whether it's transferring files or running commands—is encrypted and protected from prying eyes.
Here's a quick breakdown of the SSH process:
- Key Exchange: Your computer and the remote device exchange public keys to authenticate each other.
- Encryption: Once authenticated, all communication is encrypted using algorithms like AES or Blowfish.
- Command Execution: You can now run commands on the remote device as if you were sitting right in front of it.
Why SSH for RemoteIoT Devices?
So, why should you use SSH for your RemoteIoT devices instead of other methods? Well, let me tell ya, SSH is like the Swiss Army knife of remote access protocols. It's secure, versatile, and widely supported by most IoT devices. Plus, it comes with a ton of features that make managing your IoT fleet a breeze.
Here are a few reasons why SSH is the go-to choice for RemoteIoT devices:
Read also:Internetchicks Your Ultimate Guide To Digital Female Empowerment
- Security: SSH encrypts all communication, keeping your data safe from hackers and cyber threats.
- Reliability: SSH connections are stable and can handle intermittent network issues without dropping.
- Flexibility: You can use SSH to transfer files, run scripts, and manage configurations—all from a single interface.
SSH vs. Other Protocols
Now, you might be wondering how SSH stacks up against other remote access protocols like Telnet or FTP. Let's break it down:
- Telnet: While Telnet is simple and easy to use, it lacks the security features of SSH. All communication is sent in plain text, making it a no-go for sensitive IoT data.
- FTP: FTP is great for transferring files, but it's not encrypted, which means anyone can intercept your data. SSH's SFTP (Secure FTP) is a much safer alternative.
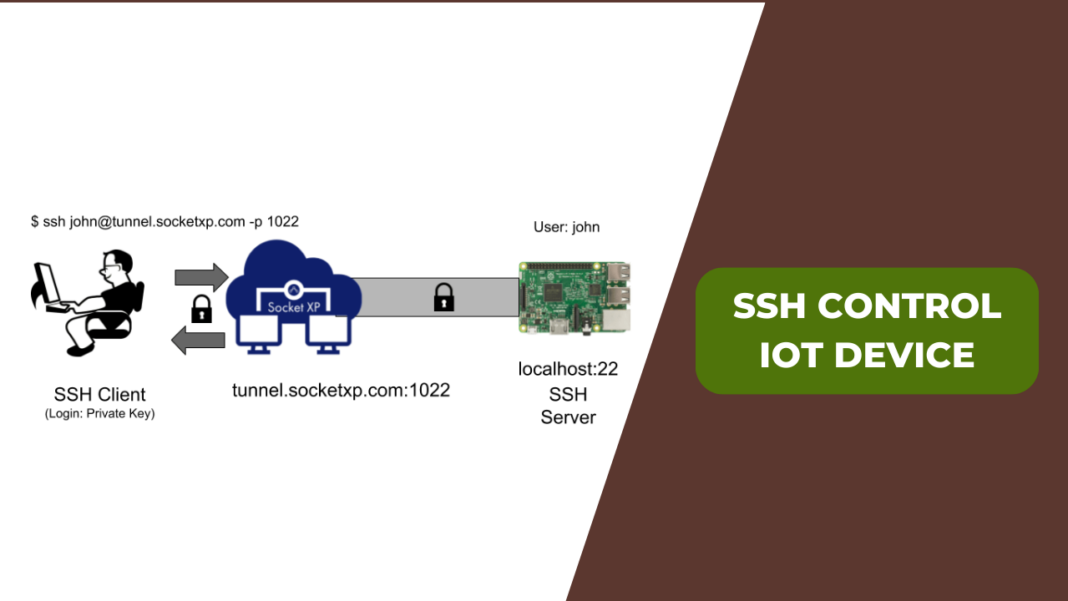
Setting Up SSH on Your RemoteIoT Device
Alright, let's get our hands dirty and set up SSH on your RemoteIoT device. Don't worry, it's easier than you think. Most IoT devices come with SSH pre-installed, but you might need to enable it first. Here's a step-by-step guide to get you started:
Enabling SSH on Your Device
First things first, you need to make sure SSH is enabled on your RemoteIoT device. Depending on the device, this can usually be done through the web interface or the command line. Here's how:
- Web Interface: Log in to your device's web interface and look for the SSH settings. Enable SSH and save the changes.
- Command Line: If you have physical access to the device, you can enable SSH using the command line. Just type
sudo systemctl enable sshand you're good to go.
Connecting to Your Device
Now that SSH is enabled, it's time to connect to your RemoteIoT device. Here's how:
- Using a Terminal: Open your terminal and type
ssh username@device_ip. Replaceusernameanddevice_ipwith the actual credentials of your device. - Using an SSH Client: If you're on Windows, you can use tools like PuTTY or MobaXterm to connect to your device. Just enter the IP address and credentials, and you're in.
Securing Your SSH Connection
Now that you've got SSH up and running, it's time to lock it down. Security should always be your top priority, especially when dealing with IoT devices. Here are a few tips to keep your SSH connection as secure as possible:
Use Strong Passwords
This one's a no-brainer, but it's worth repeating. Use strong, unique passwords for your SSH accounts. Avoid using common passwords or ones that are easy to guess. And if you're feeling extra cautious, consider enabling two-factor authentication (2FA) for an added layer of security.
Disable Root Login
Root access is powerful, but it's also a prime target for hackers. To minimize the risk, disable root login over SSH. Instead, create a regular user account with sudo privileges. Here's how:
- Open your terminal and type
sudo nano /etc/ssh/sshd_config. - Find the line that says
PermitRootLogin yesand change it toPermitRootLogin no. - Save the file and restart the SSH service with
sudo systemctl restart ssh.
Troubleshooting SSH Issues
Even the best-laid plans can go awry, and SSH is no exception. If you're having trouble connecting to your RemoteIoT device, here are a few common issues and how to fix them:
Connection Refused
If you're getting a "Connection refused" error, it could mean that SSH isn't running on your device. Check the SSH service status with sudo systemctl status ssh and restart it if necessary. Also, make sure the device's firewall isn't blocking incoming SSH connections.
Permission Denied
A "Permission denied" error usually means that your credentials are incorrect. Double-check your username and password, and make sure you're using the right IP address. If you're still having trouble, try resetting your SSH keys or enabling password authentication temporarily.
Advanced SSH Features for RemoteIoT
Once you've got the basics down, it's time to explore some of SSH's advanced features. These tools can take your RemoteIoT management to the next level and make your life a whole lot easier.
SSH Tunneling
SSH tunneling lets you forward traffic from one device to another through an encrypted SSH connection. This is particularly useful if you need to access a service on your RemoteIoT device that's not exposed to the public internet. Here's how:
- Open your terminal and type
ssh -L local_port:destination_host:destination_port username@device_ip. - Replace
local_port,destination_host,destination_port, andusername@device_ipwith the appropriate values for your setup.
Best Practices for SSH Management
Managing SSH connections for your RemoteIoT devices can be a bit overwhelming, especially if you're dealing with a large fleet. Here are some best practices to help you stay organized and secure:
Regularly Update Your Devices
Keeping your devices up to date is crucial for maintaining security. Regularly check for firmware updates and apply them as soon as they're available. This ensures that any vulnerabilities are patched and your devices are as secure as possible.
Monitor SSH Logs
SSH logs can provide valuable insights into who's accessing your devices and when. Set up log monitoring to keep an eye on suspicious activity and take action if anything looks fishy. Tools like Logwatch or Splunk can help automate this process.
Automating SSH Tasks
Automation is your best friend when it comes to managing RemoteIoT devices. By automating repetitive SSH tasks, you can save time and reduce the risk of human error. Here are a few ways to get started:
Using SSH Keys
SSH keys are a great way to automate authentication without having to enter passwords every time. Here's how to set them up:
- Generate a key pair with
ssh-keygen. - Copy the public key to your RemoteIoT device with
ssh-copy-id username@device_ip. - Test the connection to make sure it works without a password.
The Future of SSH in IoT
As IoT continues to grow, so does the importance of secure remote access. SSH will undoubtedly play a key role in this evolution, providing the foundation for secure communication between devices. But what does the future hold for SSH in the world of IoT?
One trend to watch is the rise of quantum computing, which could potentially break current encryption methods. To stay ahead of the curve, researchers are already working on quantum-resistant algorithms that will keep SSH secure for years to come. Additionally, advancements in AI and machine learning could lead to smarter SSH tools that can predict and prevent security threats before they happen.
Conclusion
Well, there you have it—your ultimate guide to mastering RemoteIoT device SSH tutorial. From setting up SSH to securing your connections and automating tasks, we've covered everything you need to know to take control of your IoT fleet. Remember, security is key, so always stay vigilant and keep your devices up to date.
Now, it's your turn to put this knowledge into action. Whether you're managing a